✏️ Written by Simon Vanhaverbeke, Cloud Engineer at Devoteam G Cloud
This article is based upon two talks during the Kubecon+CloudNativeCon 23 conference in Amsterdam: “The hacker’s guide to Kubernetes” and the “Anatomy of a Cloud Security Breach“
A popular theme this year was security. The usage of Kubernetes and cloud providers, in general, has increased a lot these last few years. This also means that attackers have started changing their targets from old-school on-premise systems to cloud environments. Lots of sessions talked about what extra steps could be taken to secure environments, there were also demonstrations on how some vulnerabilities in older versions of Kubernetes allowed attackers to get access to your cluster with ease and sessions showing how attackers have created new strategies to attack your cloud environments.
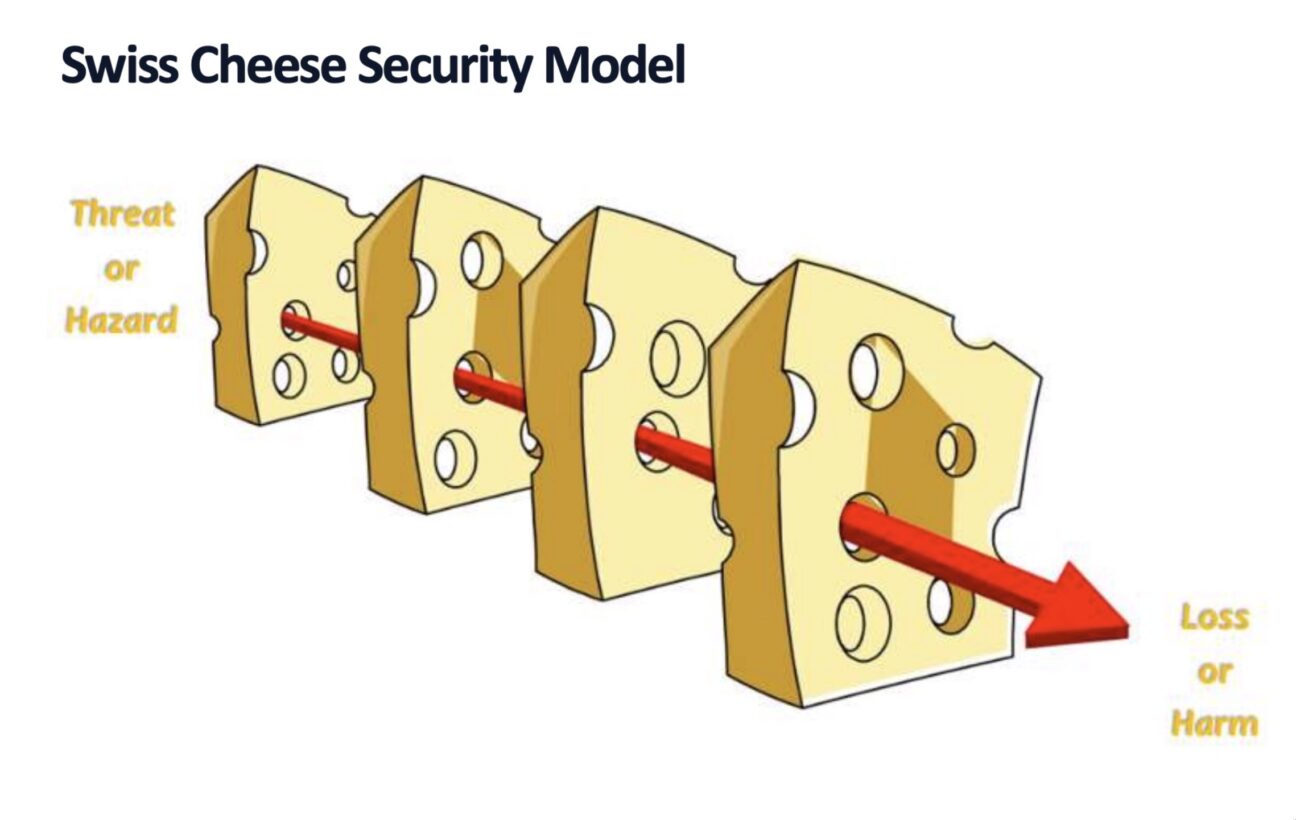
We see attackers still go for ransomware attacks when for example databases or storage buckets get compromised. But attackers also make use of features which attracted us to the cloud in the first place, namely the ease of creating new resources. With these new resources, for example, new virtual machines or new pods on clusters that autoscale, attackers can quickly set up crypto miners which gives a much faster return on their attacks.
Does this mean that you should start avoiding cloud environments? No, not at all, but it does mean that you should make sure that your cloud workloads have been adequately secured, which isn’t done the same way as on-premise.
So here are some key recommendations for you:
- It’s being said so much, but implemented so little: least-privileged credentials. Make sure that once credentials are compromised that an attacker can do as little as possible with it.
- Do not run containers as root, making sure that if a container is compromised that no privilege escalation is possible.
- Don’t trust any external sources and always verify these sources. For example, when using public container/machine images, avoid them if possible and always perform security checks before running such workloads.
- Monitor and log every angle of your environment to detect strange activity.
- Keep all your software up-to-date to avoid vulnerabilities. When you’re waiting for a patch, make sure to put mitigating controls in place.
- Properly store secrets. Make sure secrets are stored in secure locations with very limited access.

Need help securing your cloud environment?
Devoteam G Cloud has got you covered! The expert team can help you implement the best security practices, including least-privileged credentials, container security, and monitoring. Contact us now to learn more!