Understanding current security issues is essential to carry out relevant transformation projects. In this article, we’ll introduce the zero trust concept and its implementation by Google: BeyondCorp. Read this article to better understand the different components of this new security paradigm.

Article written by Victor de Coninck, Cloud Security Engineer at Devoteam G Cloud
The zero trust concept
IT security is one of the central issues for business leaders around the world. A loss of one million data files costs roughly 25 million dollars. Lose double, pay five times as much.
Traditional IT security is often compared to a medieval castle with a thick-walled fortress surrounded by a moat, with a single, heavily-guarded entry and exit point. Everything outside of the wall is considered dangerous, whereas everything inside the wall is reliable. Whoever manages to cross the drawbridge will have access to the castle’s resources. The same goes for traditional IT networks. If the firewall is put in danger, the entire internal network is exposed.
Technological evolution has made the presumption of trust not only problematic but also unnecessary. Even before the COVID-19 pandemic which made remote work the new normal for the majority of businesses, the widespread usage of mobile phones, clouds and other advanced technologies expanded businesses beyond their perimeter, which made new sources of attacks emerge.
The ideas of this perimeter security model no longer work: the perimeter is not only the business’ physical place anymore, and it is no longer a protected and secure place to house data.
In order to address the issue of “homemade” security and adapt to the new digital landscape, businesses must adopt a new security philosophy: the idea of zero trust.
The end of perimeter security
With sources of attacks being more and more diverse, it is now better to assume that an internal network is as dangerous as the public internet. The implicit trust based on the network perimeter has become insufficient.
Remote work, the adoption of the cloud and other trends are speeding up in all businesses and are creating more and more scenarios in which only the connection established from a so-called “secure” IP address is sufficient to access the company’s network (e.g. VPN). This process, known as backhauling, reinforces the myth that perimeter-based security was initially effective. However, trusting any user who could have access to a network weakens the security of a business.
Login details can be put in danger
Phishing campaigns are often launched on a company-wide basis. From that moment on, if an employee’s login details are recovered, anyone who has them can use them and connect “securely” without being detected.
Devices can be put in danger
According to the 2019 Symantec Internet Security Threat Report, 1 out of 36 devices used in companies are likely to be infected.
This includes devices that were rooted or jailbroken due to a suspicion of installed malware, but also professional hardware.
As a result, legitimate users on infected devices can, without realising it, expose sensitive resources to hackers through their own business network access.

A secure network no longer exists
IP addresses help to determine that a user is requesting access from a “trusted network”. Unfortunately, depending on this data alone is not enough, as 30% of breaches imply internal actors. The entire system must be protected.
A firewall is no longer sufficient
The myth of a safe environment behind a firewall is dangerous.
First of all, the network could already have been a victim of a breach that might have gone unnoticed. Securing this point only and letting the flows circulate freely within the private network is therefore no longer appropriate.
The zero trust philosophy
The impression of security can be an illusion, and the more you believe in this impression, the more vulnerable you become.
Security protocols that place unlimited trust in any network user are basically giving any user in the network a chance to cause damage in an equally unlimited way.
Implicit trust based on the network perimeter is therefore dangerous for the business. If this security is breached, the potential damages are endless.
To overcome these breaches, new methods and technology were invented to introduce the zero trust philosophy.
The strategic concept of zero trust is used by security managers and guarantees that their companies remain completely protected, despite the new operating modes and new market conditions that have emerged over the years.
By encouraging companies’ security teams to rely less on the traditional perimeter model and more on new security processes and technologies, the zero trust principles can be defined by the following five points:
- Any network is considered hostile by default
- Internal and external threats are always present in the network
- Being inside an internal network is never an absolute guarantee of trust
- Each terminal, user and network flow must be authenticated and authorised
- Security policies must be dynamic and defined from as many data sources as possible
From the network to the micro-perimeters
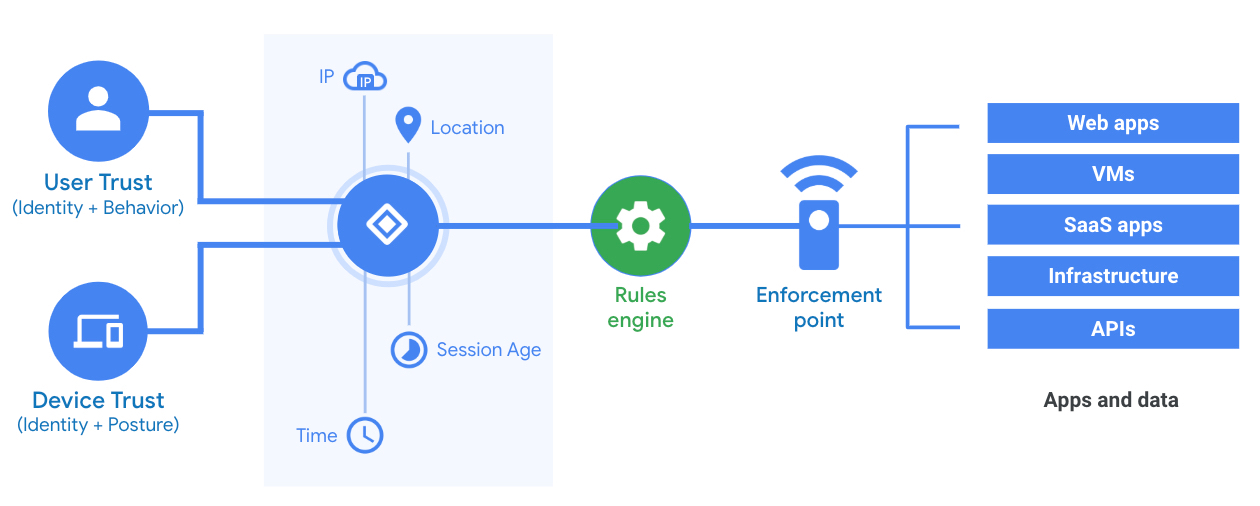
Zero trust limits the impact of unworthy parties. Rather than just determining whether an employee is on the company’s network or not, other aspects such as the risk profile of the employee, the device and the resources accessed are taken into account.
By reducing the perimeter network to micro-perimeters, zero trust allows you to apply security measures for each category of resources according to the risks.
Intelligent trust
With each access request, the continuous assessment of behaviour during the sessions ensures that trust never lasts long and is not binary.
This is done by calculating a risk score using signals. The user could then be redirected to adaptive access paths such as : authorisation, re-authentication, enhanced re-authentication, partial authorisation, refusal, and so on.
Access issues are therefore more open than before as they guarantee a more advanced control, all the while improving the user’s experience.
VPNs are long gone, long live the internet
Adopting a zero trust approach means improving professional agility, guaranteeing that the business will be able to adopt and quickly use new technologies, and achieve their digital transformation goals.
Backhaul is no longer necessary to implement. Organisations can take advantage of the full spectrum of infrastructure, application and data deployment options: with zero trust, you are able to choose between on-site data centres, private clouds, public clouds and everything in between, depending on what is more appropriate for a particular resource.
By choosing an implementation adapted to each resource, businesses canoptimise management and hosting costs by reducing licensing costs for VPNs and other perimeter-based tools.
The key features needed for zero trust
In general, six essential control categories can be defined for a zero trust security system. These different components ensure that only authenticated devices and users are authorised to use applications and other resources.
All of these components are present in Google Workspace and Google Cloud Platform, which allow a standardised implementation of the concepts, whether it be on a private, public or hybrid cloud or still in an on-premise data centre.
Strong identification and authentication
All users must be managed in user and group databases that give the systems the appropriate information at the time of access (position, responsibilities, role, etc.). This guarantees protection for all users and resources.
Google’s IAM component lets you classify users in groups, organisational units and corporations for a more precise identity management. Authentication through Google’s single sign-on (SSO) also provides a high level of security through multi-factor authentication (MFA). You can also use your own SSO or even interface with Google’s SSO on your own on-premise applications.
Security of access devices
It’s often a legitimate user who accidentally exposes their company to a high level of risks when they access resources from endangered devices. That’s why Mobile Device Management (MDM) is just as important as verifying a user’s identity; it’s recommended that each device is issued and actively managed by the company.
BeyondCorp introduces endpoint management which allows personal devices to be authorised or not.It demands safer passwords, deletes data from remote devices, manages iOS applications, uses professional Android profiles and so much more, like DLP (Data Loss Prevention) measures, directly from the device.
Active devices are recorded and uniquely identified through certificates, they are approved by administrators and their status (updates, applications, encryption and so on) is automatically verified.

Network security
Segmenting services, avoiding lateral movements between segments, 802.1X and so on… These are basic security principles that are obviously part of zero trust. But the main part, conceptually inherent to zero trust and one of its five basic principles, is removing the trust given to the network.
To make remote and local access equal, local users are placed in a limited network strictly partitioned by ACLs from the rest of the local network.
Workload security
Whether these access requests are local or remote, they are then verified by a proxy software which takes care of evaluating the user’s risk profile, information regarding the end device, the log-in details and the associated authorisations, and decide whether access is allowed or not.
BeyondCorp allows you to manage all your applications and APIs (on-premise or cloud) through a single console in Google Cloud Platform: Identity Aware Proxy (IAP). IAP can be found in Google’s secure infrastructure and is based on various user data and device inventories, as well as the different levels of access, security policies and other static and dynamic rules put in place.
Transaction security
Some transactions obviously present more risks than others, and so should be closely monitored and treated consequently. It must be possible to ensure that high-risk transactions are verified while at the same time being able to automatically recognise abnormal transactions.
BeyondCorp and Google Workspace are in charge of this surveillance, by proposing intelligent tools for analysing e-mail flows and connections, and other work insights from the admin interface, raising alerts and other automatic response mechanisms: blocking a device or an IP, redirection of flows to a quarantine zone, etc.
Data protection
New rules regarding the confidentiality of user data arise in order to guarantee that data is encrypted where it needs to be and that users still have control over their personal information.
In the context of Google, the Data Loss Protection components are present both in Google applications and in endpoints, which prevents certain resources from being downloaded.
Some more innovative features will even identify the presence of some data in email attachments: the presence of debit cards, ID documents, invoices in attachments among others can be verified, thanks to Google’s highly powerful photo recognition.
Cloud, thousands of interconnected services, APIs, IOT, ineffective perimeter defences, new forms of attacks, mobility of employees and devices… All of this requires a new security approach which focuses on identities, access and data. The implementation of a zero trust approach is mainly based on a review of identity and access management policies and processes.
Systematicity is zero trust’s number one enemy. Here, the goal is to allocate rights dynamically, with a broader and more informed view of the user’s authenticity. Identity and Access Management (IAM) is therefore vital but isn’t enough on its own, other components must be added to it.
One of these components is multi-factor authentication (MFA), necessary to close the single-sign-on (SSO) breaches, essential in the SaaS era. Privileged Access Management (PAM) and User and Entity Behaviour Analytics (UEBA) are often put in place in top of a SIEM, a coordination of cloud access strategies (CASB, Cloud Access Security Broker), mobile device management (EMM, Entreprise Mobility Management) and threat response solutions.
All these components exist, some for a long time, others are new concepts but beyond technologies. The zero trust approach is, above all, a culture to be instilled in administrators, users, and the company which needs support with such a significant change.
The BeyondCorp offer combines these different components. Devoteam G Cloud’s expertise will help you to make the right decision according to your needs in order to define an optimised and evolutionary approach to zero trust.
Do you want to discuss your own Security challenges with us?
Get in touch with
Mark De Winne
Google Cloud Business Developer at Devoteam G Cloud