What is it

Conditional Access can be used to ensure that only authorised users are able to access sensitive resources/applications and to prevent unauthorised access from potentially compromised devices or networks. It can also be used to enforce security policies and compliance requirements, such as requiring multi-factor authentication for certain resources or blocking access from specific regions.
One key aspect of Conditional Access is the ability to be “conditionally aware.” This means that the system is able to take into account the context of the request, such as the user’s identity, the device being used, and the location. It uses this information to make an informed decision about whether to grant access.
Conditional Aware Access is a main building block for a secured Zero Trust environment, also known in Google Workspace / Cloud as Beyondcorp Enterprise
Benefits of having Conditional Aware Access in your environment are for example:
- Enhancing your overall system security
- Protecting company data
- Privileged & controlled access
How does it work
Let’s start with an example: a user attempting to access a sensitive resource from an unfamiliar device or location might be prompted for additional authentication, such as a one-time passcode sent to their phone. On the other hand, a user accessing the same resource from a trusted device and location might be granted access without any additional prompts.
Most Identity providers supply their own form of Conditional Aware Access, as does Google Workspace & Google Cloud.
Google Workspace focuses on delivering a simple to manage set of security features that integrate fully with other Google services and also 3rd party applications connected to the platform. It gives end-users a smooth user experience and it makes them autonomous by informing them along the way which policies must be met for each configured application or service.
Google Cloud can even secure your infrastructure by establishing an encrypted tunnel over which you can forward SSH, RDP, and other traffic to these VM instances.
How far does it go
Conditional Access can be a powerful tool for securing access to resources, but it is important to carefully consider the policies and conditions that are put in place. Too many restrictions or overly strict policies can create a burden for legitimate users, while too few can leave resources vulnerable to unauthorised access. By being “conditionally aware,” organisations can strike a balance between security and convenience, protecting their resources while still allowing authorised users easy access.
Most providers supply a basic set of policies to enforce over your environment and allow for custom code in case of advanced use cases. Google Workspace allows for Common Express Language (CEL) to be used in exploring this.
Here are two examples:
This example uses device attributes to require both disk encryption and screen lock to be enabled. In addition, the device has to be approved by administrators.
device.encryption_status == DeviceEncryptionStatus.ENCRYPTED &&
device.is_secured_with_screenlock &&
device.is_admin_approved_device
In this case, only devices meeting the above requirements would be able to access the attributed applications or environments
In this second example, contractors get access to corporate resources only from a specific corporate IP address range.
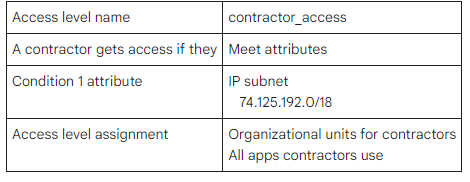
When this contractor attempts to access company applications from another location than the corporate location (hence the IP subnet), they will be refused access.
Conclusion
In conclusion, Conditional Aware Access is a powerful security feature that can help organisations protect their sensitive resources and data from unauthorised access. By setting specific conditions for granting access, organisations can strike a balance between security and convenience, ensuring that only authorised users are able to access their resources. If you want to enhance the security of your cloud applications, consider implementing Conditional Aware Access.

Start taking the necessary steps to protect your organisation’s data and resources today.
Contact us to know more about it or request guidance on how to implement these Conditional Cloud Aware Access features and policies.