In today’s fast-changing digital world, what really worries businesses is how safe their digital assets are. They’re concerned about sneaky access to their important info, possible data leaks, and losing control over valuable stuff. With more remote work and different devices being used, they fear cyber trouble might hit. Finding the right balance between easy teamwork and strong security is tough. In this article, Devoteam’s expert highlights how you can use Google Workspace to keep your business secure.
Prefer to watch?
Dive into the Future of your digital workplace with this session recording on ‘Secure Endpoint Management’. Or discover the webinar series, where you’ll discover how Google Workspace changes IT operations, boosts security, and drives efficiency.
Adapting to the changing work environment: from a conventional set-up to a cloud-powered workplace
Picture a workplace where flexibility reigns supreme – where collaboration knows no bounds, and accessing your work from any device is a reality. This transformation is underway, and successful enterprises are at the forefront of this shift. Embracing the cloud is the key, liberating you from the confines of traditional setups.
The traditional set-up
In the traditional setup, businesses often rely on existing approaches, built for on-premise environments. Employees typically need to be at a specific location to access data and applications. Collaboration might be limited to certain hours or specific tools. Or they are using VPNs and inconvenient authentication methods to get access. This approach, while familiar, comes with limitations. Security often centres around perimeter defences, like firewalls, to protect the central hub where data is stored. It’s like building a fortress around a castle – effective to some extent, but vulnerable if any part of the defences is breached.
The Cloud Set-up
Now, contrast that with the cloud setup. With the cloud, security is no longer solely about protecting a central location. Instead, it’s about safeguarding data wherever it’s accessed or stored. It’s a bit like guarding every door to the castle equally, rather than just focusing on the main gate. This dynamic approach, often referred to as a “zero trust” model, means that every access point is treated as potentially risky, requiring thorough verification.
The key difference here is that security is integrated into every aspect of the cloud setup. It’s not an afterthought or a separate layer; it’s woven into the fabric of how data is managed, shared, and accessed. This level of integration provides a more adaptive way to protect sensitive information. And that’s a game-changer.
So, the shift to the cloud isn’t just about convenience and collaboration. It’s also about redefining security – from a fixed fortress approach to a dynamic, adaptable, and data-centric strategy. As we delve deeper into the domain of workspace security within Google Workspace, you’ll discover the intricacies of this transformation and how it impacts your organisation’s security posture.
Empowering endpoints: leveraging the Chrome ecosystem
Endpoints are the cornerstones of your digital workspace, and mastering them is crucial. In a nutshell, we see 4 distinctive endpoints in today’s work environment:
- ChromeOS (Chromebook): Easily manageable through the Google Admin Console, it offers advanced security features, zero-touch enrollment, and granular device controls.
- Windows 10: Managed via the Google Credential Provider for Windows (GCPW), enabling policies, updates, and custom settings for enhanced control on any Windows 10 device.
- MacOS: Best practices include managing the Chrome Browser and utilising third-party integrations like Jamf for endpoint management.
- Chrome Browser: Available on multiple operating systems, it empowers employees to access web resources securely, making it ideal for remote, extended, and hybrid workforces.

ChromeOS (Chromebook):
ChromeOS, an operating system built on the Chromium platform, is a cornerstone of endpoint management in Google Workspace. Notably, ChromeOS offers a high degree of configurability, making it easily manageable through the intuitive Google Admin Console. This streamlined management process ensures that IT administrators can efficiently oversee a fleet of ChromeOS devices, optimising productivity and security.
Furthermore, ChromeOS introduces the concept of “zero-touch enrollment.” With this innovative feature, administrators can effortlessly drop-ship devices directly to employees. Upon receipt, employees can seamlessly sign in, triggering automatic device enrollment and configuration. This approach enhances efficiency and minimises the need for extensive setup processes.
The security of ChromeOS is another highlight. Advanced security features are integrated, allowing administrators to remotely wipe or disable devices if necessary. Additionally, fine-grained control is attainable through granular device controls. From enabling single sign-on to configuring Wi-Fi networks, administrators can tailor settings to align with the organisation’s security posture.
Chrome Browser: Connecting the Workforce Across Devices
The Chrome Browser emerges as a versatile tool for organisations seeking secure and efficient endpoint management. Designed to meet the needs of a cloud-based enterprise, the Chrome Browser empowers employees to access web resources from any device, making it particularly advantageous for remote, extended, and hybrid workforces.
Key security features are embedded within the Chrome Browser. It enables administrators to protect both managed and unmanaged devices, making it conducive to BYOD (Bring Your Own Device) strategies. Access to software-as-a-service (SaaS) applications is safeguarded, ensuring data integrity and user privacy.
Notably, the Chrome Browser offers comprehensive reporting capabilities, enabling administrators to gain insights into browser versions, settings, and device details. This information contributes to informed decision-making and supports compliance efforts.
Windows 10: Enhanced Control and Customization through GCPW
Windows 10, a common operating system in many organisations, can be effectively managed within the Google Workspace ecosystem using the Google Credential Provider for Windows (GCPW). This integration empowers administrators to enforce policies, manage automatic updates, and implement custom settings with precision.
Administrative permissions are a crucial aspect of Windows device management. Through GCPW, administrators can set users’ permission levels, ensuring that access is aligned with job roles and responsibilities. Moreover, custom settings enable fine-tuning of the user experience. Administrators can block specific applications, disable USB drives, and even define screen lock timeout parameters. These capabilities contribute to a controlled and secure Windows 10 environment.
One standout feature of GCPW is its compatibility with Google Cloud identity. This allows employees to seamlessly log on to Windows devices using their Google Cloud credentials, enhancing convenience and streamlining access management. Additionally, administrators can exert domain limitations, further enhancing security.
MacOS: Leveraging Chrome Browser and Third-Party Integrations
MacOS presents unique challenges in endpoint management. With the right approach, you can ensure control and security. One effective strategy involves focusing on managing the Chrome Browser, which aligns with Google’s cloud-based enterprise philosophy. The Chrome Browser, built on open-source Chromium code, provides a consistent and secure browsing experience across various operating systems.
To enhance MacOS management, organisations can leverage third-party integrations such as Jamf. This integration augments management capabilities and provides additional options for policy enforcement and security measures.
Control over Mobile Devices
Mobile devices are an integral part of the modern workspace, and ensuring their security is essential. Google Workspace steps up to the plate with solutions for both Android and iOS. From app management to security settings, you’re in the driver’s seat. Whether it’s company-owned or part of a bring-your-own-device strategy, you retain control, ensuring compliance and data security.
Mobile Device Management with Google Workspace
Google Workspace’s mobile device management ensures a secure and controlled environment:
- Basic Management: This level includes screen lock enforcement, basic passcode policies, remote data wipe, device inventory, and audit logs. No device policy agent/enrollment is required, ensuring simplicity.
- Advanced Management: Elevate security with advanced controls. This level encompasses advanced security measures, application management, device wipe, optional device approval, and the implementation of Android work profiles.
A standout feature of Google Workspace’s mobile management is the ability to enforce work profiles on devices. This separation effectively isolates work and personal environments, allowing for data protection and management, monitoring, and security.
Device Inventory
Administrators have good device oversight, including:
- Viewing device details such as type, model, last sync date, user information, and more.
- Monitoring management levels, encryption status, and sync dates.
- Identifying potential risks posed by installed apps, including harmful applications.
In conclusion, Google Workspace ensures mobile security by providing a range of management options for Android and iOS devices. From basic controls to advanced security measures, administrators can maintain a secure and productive mobile workspace while separating work and personal environments where needed.
Beyond Corp: Zero Trust and Data Protection
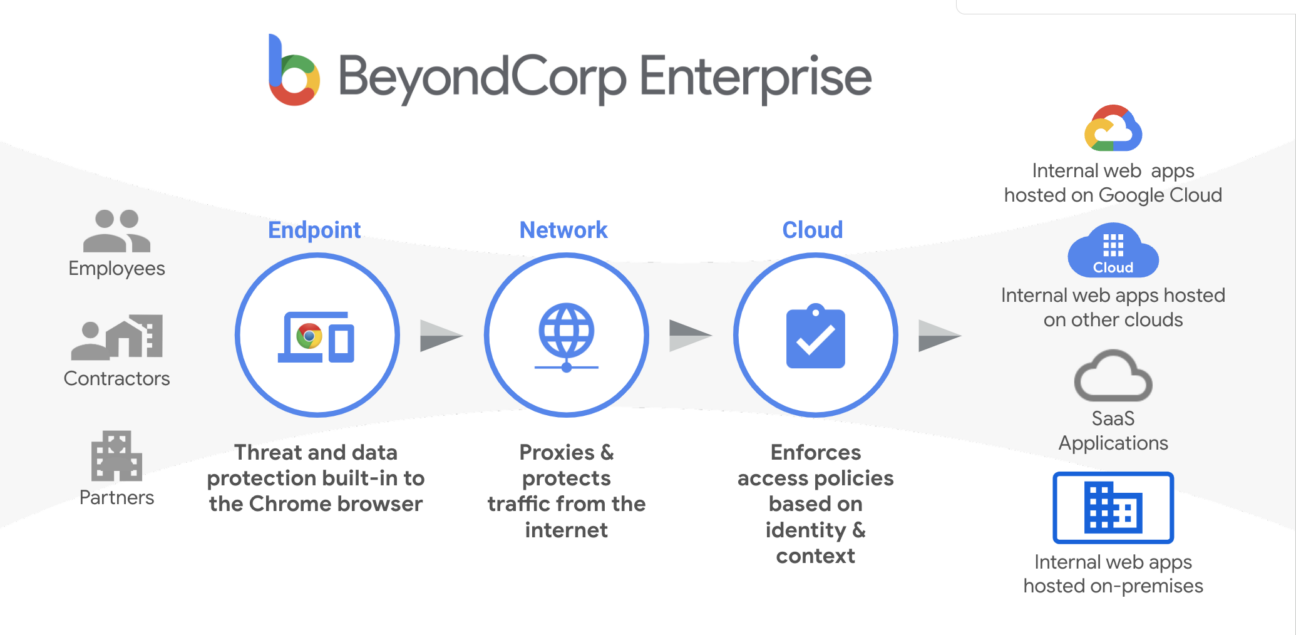
So what’s next? The future is already here under the name of Google’s Beyond Corp. This revolutionary zero-trust philosophy redefines data protection, developed and used by Google themselves. By leveraging user and device context, and fortifying internal applications, it propels security to new heights. The spotlight is on access control and compliance, all orchestrated seamlessly through the Google admin console.
Context is king
BeyondCorp stands as a beacon of security in a world where connections transcend boundaries. It safeguards internal apps hosted on various platforms, enforces access policies based on identity and context, and shields against threats. This is the security strategy of tomorrow, ensuring data protection and control in an ever-evolving digital landscape.
Context is king, and BeyondCorp orchestrates this symphony meticulously. User identity, device state, and context intricacies like IP addresses and location are at the heart of this technology. This path of information ends up in the rules engine, where it decides who can do what and get access. Whether users log in, from where, and for how long—these variables seamlessly translate into access decisions.
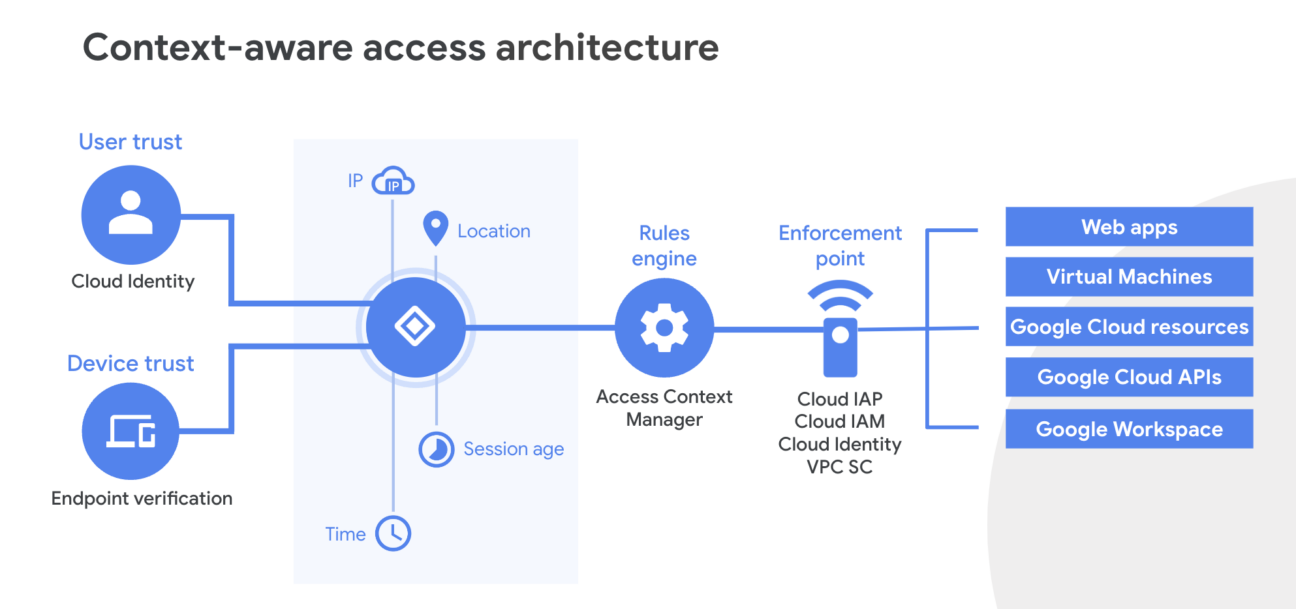
BeyondCorp goes beyond access control. Endpoint protection within BeyondCorp includes an array of robust features like real-time malware defence, and data loss prevention, all orchestrated seamlessly through the Google admin console. How does this work practically? See BeyondCorp as a data protector. It can carefully check files you upload, download, or share. Even all access to applications can be put through this rule engine. This helps those in charge make sure only allowed stuff gets through, stopping anyone from getting into personal or important info without permission.
Conclusion
In a rapidly changing digital landscape, securing valuable data is a top concern for businesses. The shift to remote work and diverse devices adds complexity to this challenge.
Google Workspace offers a powerful solution, offering efficient endpoint management across platforms like ChromeOS, Windows 10, MacOS, and the Chrome Browser. Additionally, mobile device management ensures secure access to data, while BeyondCorp’s zero-trust philosophy takes security to new heights by considering user context.

The future of workplace security is here, and with Google Workspace, businesses like yours can embrace it confidently. Ready to explore how your organisation can take advantage of this technology? Get in touch.