What is it
Three key concepts when talking about (secure) IAM:
| Identity(who are you?): | Authorisation (prove it is, in fact, you): | Authentication (who can access what) |
|---|---|---|
| Having a clear and unique identity tied to a single person/ the fact of being who or what a person or thing is. | Typically roles-based access control that defines what operations an entity can perform in the context of a specific application and flexible security policies with enforcement | Verification that an entity is who/what it claims to be using: Single sign-on; Multi-factor authentication |
Using a third-party identity provider (IdP) to assist with these together with Google Workspace can provide additional security and flexibility for managing user access to the platform, as depicted below.
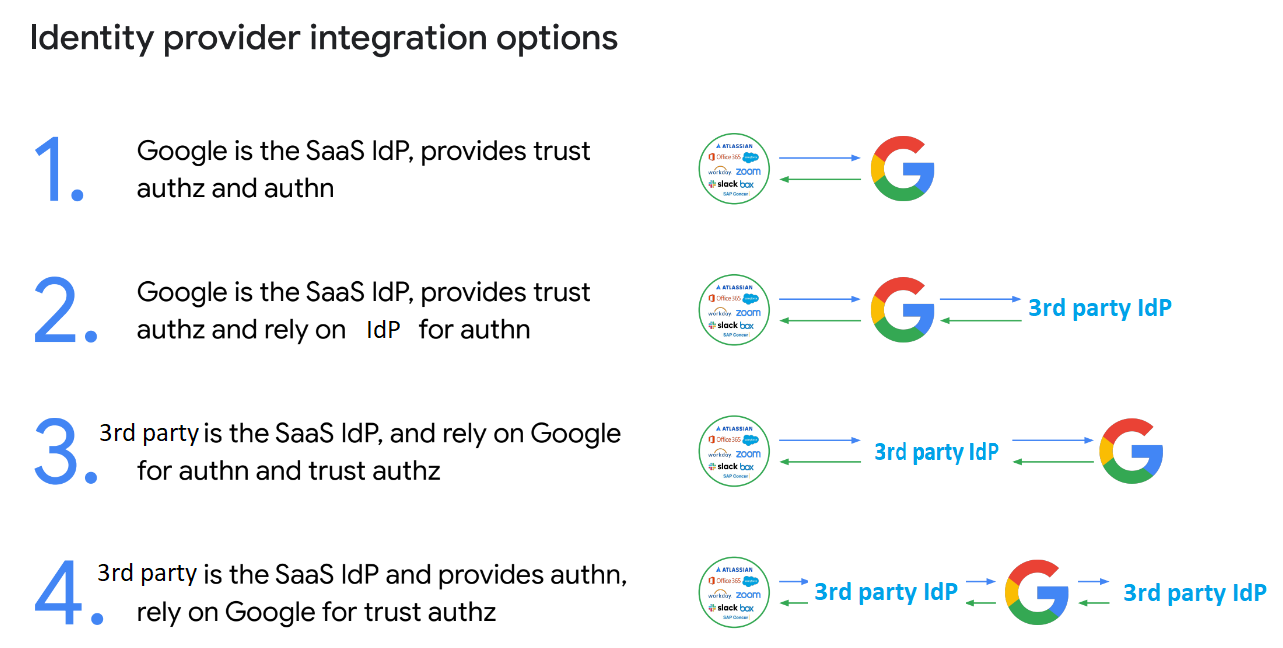
An IdP is a service that manages user authentication and authorization for multiple applications and services. This means that instead of managing user credentials and access for each individual application, an IdP can handle this centrally for all of the applications and services that it is connected to. This can save time and resources for IT teams, as well as provide an additional layer of security.
There are several third-party IdPs available that can be used with Google Workspace, including for example Okta, OneLogin, and Azure Active Directory to name a few. These providers can be easily integrated with Google Workspace using the Security Assertion Markup Language (SAML) protocol.
How does it work
Integration with a third-party IdP allows users to use the same credentials they already use to access other applications and services to access Google Workspace. This can reduce the number of passwords that users need to remember and make it easier for them to access the platform (also known as the concept of SSO).
To be able to set it up in Google you need:
- Sign-in page URL: This is also known as the SSO URL or SAML 2.0 Endpoint (HTTP). This is where users sign in to your IdP.
- Sign-out page URL (Optional): Where the user lands after exiting the Google app or service.
- Certificate: X.509 PEM certificate from your IdP. For more information on X.509 certificates, see SAML key and verification certificate.
- Change password URL (Optional): The page where SSO users will go to change their password (instead of changing their password with Google).
You can find more information here & a list of out-of-the-box supported apps here.
In addition, using a third-party IdP can also provide an additional layer of security. With any IdP, IT teams can enable multi-factor authentication (MFA) and other security features to ensure that only authorised users can access applications & Google Workspace from either the default security features provided in Google Workspace, or those from the connected IdP.
All applications can benefit from this integration when connected to the Single Sign On (SSO) feature of your Google Workspace environment, allowing you to utilise the same Authentication method to continue leveraging SSO features.
How far does it go
However, when using a third-party IdP, it’s important to pay attention to the support provided by the third party on the integration with Google Workspaces, as not all IdPs have the same level of support and integration capabilities with Google Workspace. Additionally, IT teams should also consider the cost and scalability of the third-party IdP, as well as any additional features that it may provide, such as password management and user provisioning.
Overall, using a third-party identity provider with Google Workspace can provide additional security, flexibility, and ease of use for managing user access to the platform. However, it’s important to carefully evaluate the features and capabilities of the different IdPs available and to work with a trusted provider that has a proven quality of integration with Google Workspace.

Taking Identity & Access Management to the next level would mean implementing these security features next to Conditional Aware Access so you can reach a true Zero Trust Environment, as described in Google’s Zero trust solution BeyondCorp
Starting with the entry-level licence package of Beyondcorp Essentials you can already leverage the Zero Trust philosophy over your Workspace environment and its connected services. Bringing your GCP resources in the mix will require Beyondcorp Enterprise.

Ready to take control of your identity and access management?
Get in touch today to explore how third-party identity provider integrations can enhance your security, flexibility, and ease of use for managing user access to your Google Workspace platform. Devoteam’s experts are ready with guidance on how to implement these strategies.