Did you know that you are able to see which third-party applications your users are logging in to? Did you also know that you can restrict certain google services such as Gmail, Google Drive and GCP from being accessed through their correspondent APIs? Maybe your users are logging into Tinder or Facebook with their corporate Google account. Find out how to limit Third-party application access and more in this blog post.
How a third-party application interfaces
Mainly there are 2 ways any third-party application can interface with your Google Workspace instance:
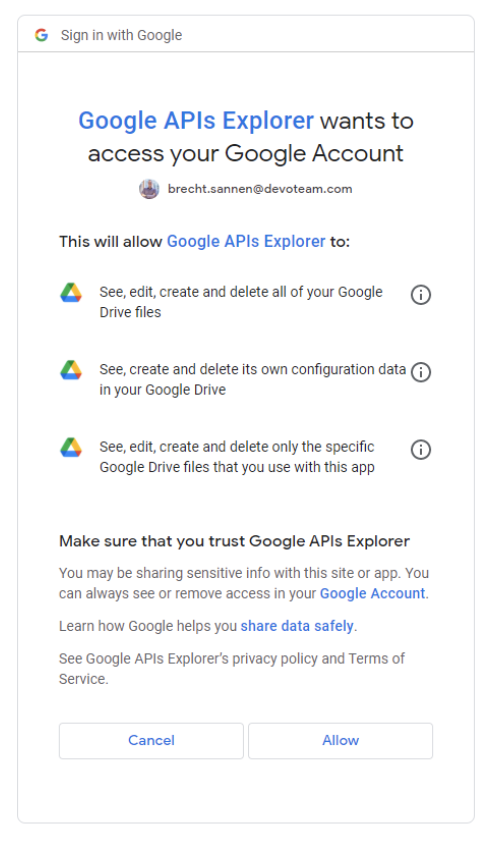
1. I as a user authorize a third-party application to access my google services (App access control)
When a third-party application seems interesting to you, you can authorize that application to access your Gmail, Google Drive, GCP and many more google services. Another example is when you create an account on a website using your google account.
There is a multitude of applications out there and that is why Google Workspace allows you to limit what applications your users are allowed to access & sign in to.
2. I as a domain administrator want to give an application the ability to impersonate users within my domain (Domain-wide Delegation)
Domain-wide delegation is a very powerful option in Google Workspace. It allows you to execute actions as if the user itself had executed it. It is mostly used for either migrations or to execute bulk administrative tasks with tools like GAM.
App access control
Nowadays anyone can create a third-party application that could interface with a Google Workspace account. Whether you find them on the Google Workspace Marketplace, the Play Store or just online, you’ve got to be careful which applications you trust. Therefore it is advised to monitor these applications and to even set up some limitations for certain Google Services.
Google Workspace gives you the opportunity to monitor & govern what third-party applications your individual users are interfacing with and allows you to limit certain high-risk Google services from being interfaced with. When you start limiting access to services & trusting applications, follow this smart process:
1. Analyze the list of all applications your users are interfacing with.
You can export all the accessed apps in your admin console to a Google Sheet. You can find the UI via this link. After you have exported it, take a look at the names, verified status & the scopes and see if there is anything suspicious there.
2. Trust the applications you know (e.g. Used by the business) and block the ones you don’t.
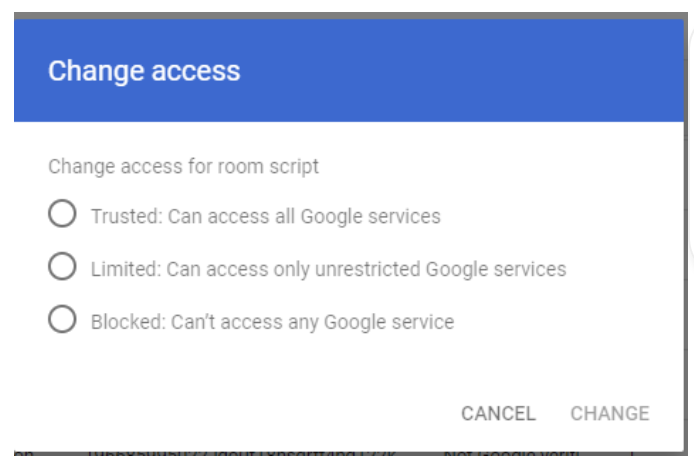
When you have an overview, you can start trusting the applications that are relevant to your business. This way you don’t block these applications from working when you execute the next step. You can label an application as trusted in this UI in the admin console by clicking on “change access” for that application.
The same goes if you want to block this application. You can click on blocked and then it is immediately blocked from accessing any service in your Google Workspace.
3. Limit the Google services that no third-party application should be able to access.
Now that you have trusted and blocked all the relevant applications, you can start looking at what “high-risk” scopes are for your business. There are 2 options when it comes to blocking services. Either you disallow anything from ever interfacing with a specific Google Workspace service or you allow trusted applications to interface with your Google Workspace service.
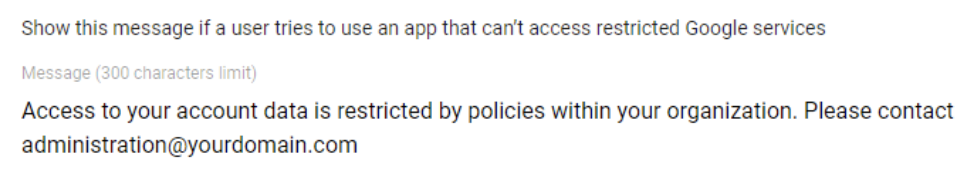
Usually, we see companies blocking Gmail, Google Drive, GCP and google calendar from being accessed by third-party applications not trusted by the organization. Currently it is not possible to limit this per OU or group. Lastly, they put up a message saying to contact a certain e-mail address or fill in a specific form to get an application on the trusted list.
Domain-Wide Delegation
Domain-wide delegation window is one of the easiest to govern in Google Workspace. You have a list of applications and the scopes they are allowed to access. Make sure you keep an eye on these scopes so that you can make sure that no unauthorized access is ever given to your entire domain.
The last thing to consider is that you don’t need domain-wide delegation to execute administrative actions in your Google Workspace. Nowadays you can give a GCP service account an admin role that allows it to execute specific tasks. This way you don’t need to impersonate an administrator for your automated administrative tasks.
In a nutshell
Keep an eye on your third-party applications interfacing with Google Workspace:
- Restrict scopes such as Gmail, Google Drive & Google Calendar to prevent data leaks.
- Understand the difference between domain-wide delegation and individual API access.
- Review your API access regularly to avoid any unauthorized access
Do you want to discuss your own Digital Workplace project with us?
Get in touch with
Mark De Winne
Google Cloud Business Developer at Devoteam G Cloud